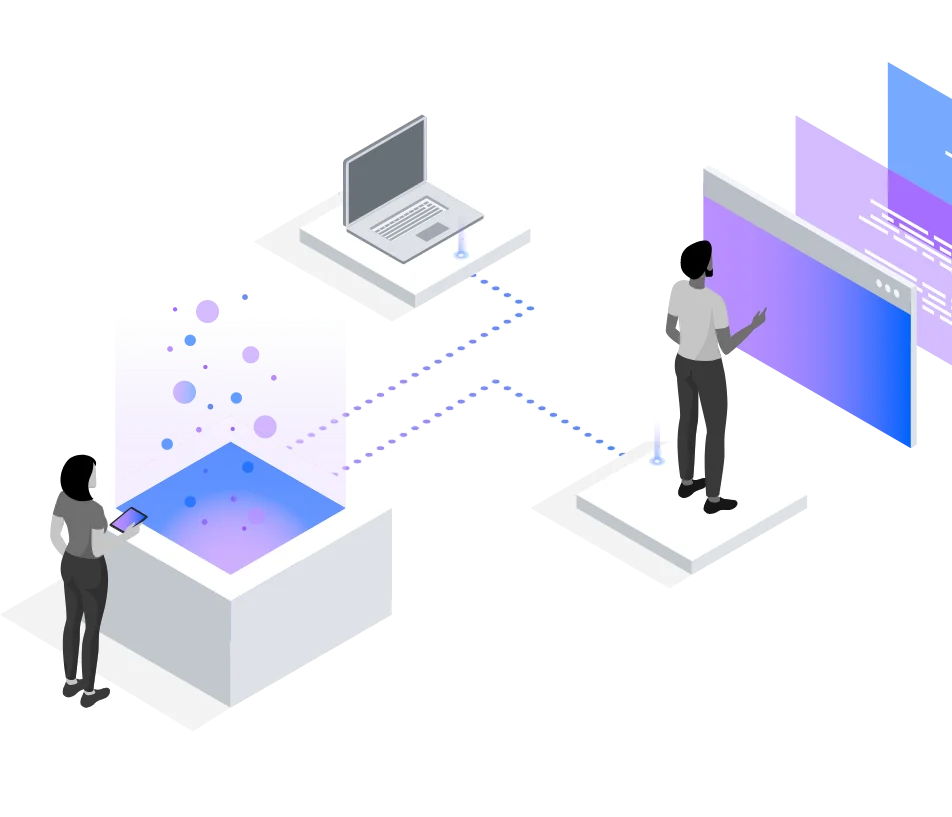
The OODA loop refers to a military-derived methodology to incident response. It is not a rigid protocol, but it’s a good outline of how effective incident response teams operate. The OODA Loop includes four steps, which are Observe, Orient, Decide, and Act, each of which are designed to help minimize the impact of security incidents.
The Observe step requires visibility into your network, your operating system, and your applications. Observing activity on your network helps you establish a basis for normal operation, so you and your tools can more effectively identify irregular activity. Uvation will stay apprised of the latest threat intelligence.
During the Orient step, your incident response team will assess the applicability of the latest security protocols and work to understand potential threats in context. They’ll also address operational issues and work to protect your network from risk.
During the Decide and Act steps, your incident response team will determine the best premeditation strategy and then put that strategy into action. They’ll manage incidents in real-time, monitor the results, and help to heal any damage. Once managed, the team will return to the Observe step.